parent
84b27a7f49
commit
018a9eab1f
@ -413,12 +413,26 @@ sudo chmod 600 ikev2vpnca.cer vpnclient.cer vpnclient.key
|
|||||||
**注:** 这些步骤由 [@Unix-User](https://github.com/Unix-User) 提供。
|
**注:** 这些步骤由 [@Unix-User](https://github.com/Unix-User) 提供。
|
||||||
|
|
||||||
1. 将生成的 `.p12` 文件安全地传送到你的计算机。
|
1. 将生成的 `.p12` 文件安全地传送到你的计算机。
|
||||||
1. 在 WinBox 中,转到 System > certificates > import.
|
|
||||||
1. 将 `.p12` 证书文件导入两次(是的,导入同一个文件两次)。
|

|
||||||
1. 在 terminal 中运行以下命令:
|
|
||||||
|
2. 在 WinBox 中,转到 System > certificates > import. 将 `.p12` 证书文件导入两次(是的,导入同一个文件两次)。检查你的 certificates panel。你应该看到 2 个文件,其中标注 KT 的是密钥。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
3. 在 terminal 中运行以下命令。将以下内容替换为你自己的值。
|
||||||
|
`YOUR_VPN_SERVER_IP_OR_DNS_NAME` 是你的 VPN 服务器 IP 或域名。
|
||||||
|
`IMPORTED_CERTIFICATE` 是上面第 2 步中的证书名称,例如 `vpnclient.p12_0`
|
||||||
|
(标记为 KT 的那一行 - Priv. Key Trusted - 如果未标记为 KT,请再次导入证书)。
|
||||||
|
`THESE_ADDRESSES_GO_THROUGH_VPN` 是你想要通过 VPN 浏览因特网的本地网络地址。
|
||||||
|
假设 RouterOS 后面的本地网络是 `192.168.0.0/24`,你可以使用 `192.168.0.0/24`
|
||||||
|
来指定整个网络,或者使用 `192.168.0.10` 来指定仅用于一个设备,依此类推。
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
|
/ip firewall address-list
|
||||||
|
add address=THESE_ADDRESSES_GO_THROUGH_VPN list=local
|
||||||
/ip ipsec mode-config
|
/ip ipsec mode-config
|
||||||
add name=ike2-rw responder=no
|
add name=ike2-rw responder=no src-address-list=local
|
||||||
/ip ipsec policy group
|
/ip ipsec policy group
|
||||||
add name=ike2-rw
|
add name=ike2-rw
|
||||||
/ip ipsec profile
|
/ip ipsec profile
|
||||||
@ -428,12 +442,12 @@ sudo chmod 600 ikev2vpnca.cer vpnclient.cer vpnclient.key
|
|||||||
/ip ipsec proposal
|
/ip ipsec proposal
|
||||||
add name=ike2-rw pfs-group=none
|
add name=ike2-rw pfs-group=none
|
||||||
/ip ipsec identity
|
/ip ipsec identity
|
||||||
add auth-method=digital-signature certificate=certificate.p12_1 generate-policy=port-strict mode-config=ike2-rw \
|
add auth-method=digital-signature certificate=IMPORTED_CERTIFICATE generate-policy=port-strict mode-config=ike2-rw \
|
||||||
peer=ike2-rw-client policy-template-group=ike2-rw
|
peer=ike2-rw-client policy-template-group=ike2-rw
|
||||||
/ip ipsec policy
|
/ip ipsec policy
|
||||||
add group=ike2-rw proposal=ike2-rw template=yes
|
add group=ike2-rw proposal=ike2-rw template=yes
|
||||||
```
|
```
|
||||||
1. 检查你的 certificates panel。你应该看到 2 个文件,其中标注 KT 的是密钥。具体请参见 [#1112](https://github.com/hwdsl2/setup-ipsec-vpn/issues/1112#issuecomment-1059628623)。
|
4. 更多信息请参见 [#1112](https://github.com/hwdsl2/setup-ipsec-vpn/issues/1112#issuecomment-1059628623)。
|
||||||
|
|
||||||
> 已在以下系统测试
|
> 已在以下系统测试
|
||||||
> mar/02/2022 12:52:57 by RouterOS 6.48
|
> mar/02/2022 12:52:57 by RouterOS 6.48
|
||||||
|
|||||||
@ -416,22 +416,23 @@ If you get an error when trying to connect, see [Troubleshooting](#troubleshooti
|
|||||||
|
|
||||||
1. Securely transfer the generated `.p12` file to your computer.
|
1. Securely transfer the generated `.p12` file to your computer.
|
||||||
|
|
||||||
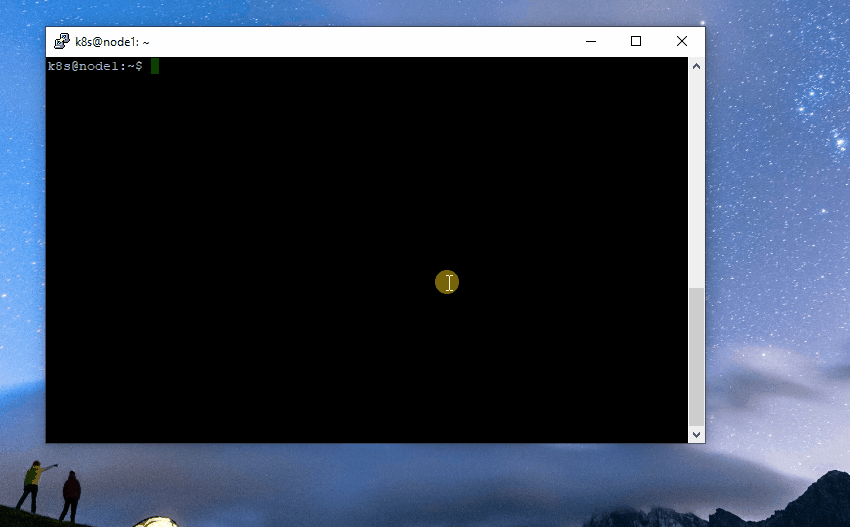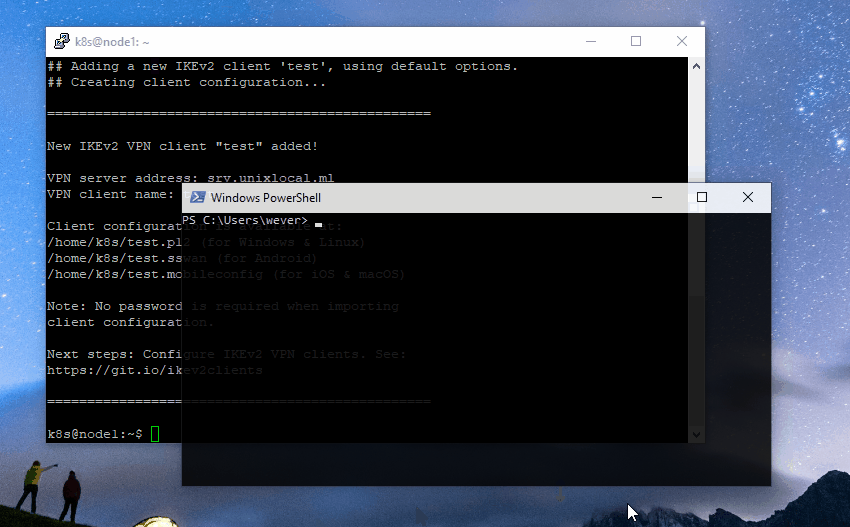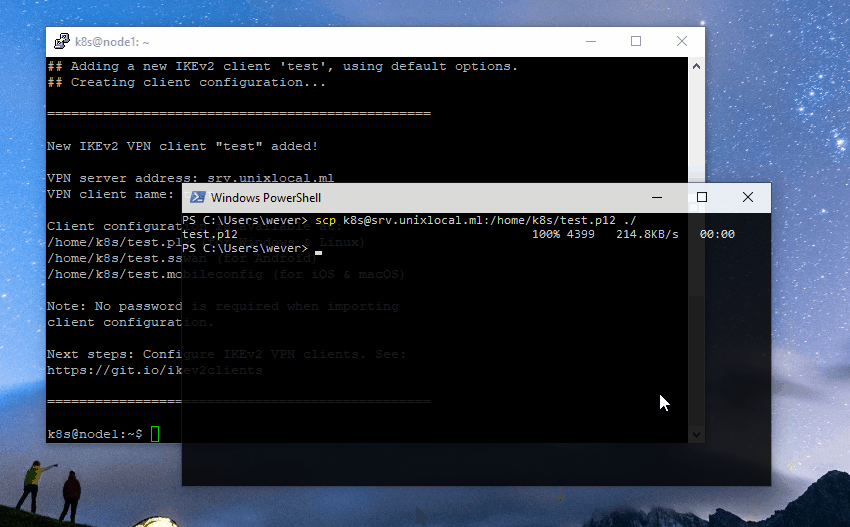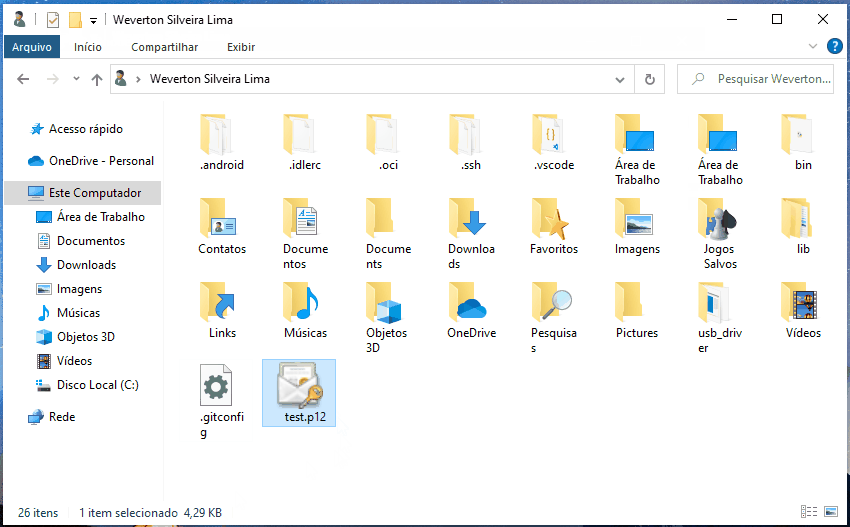
|

|
||||||
|
|
||||||
2. In WinBox, go to System > certificates > import.
|
2. In WinBox, go to System > certificates > import. Import the `.p12` certificate file twice (yes, import the same file two times!). Verify in your certificates panel. You will see 2 files, the one that is marked KT is the key.
|
||||||
2.1. Import the `.p12` certificate file twice (yes, import the same file two times!).
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
3. Run these commands in terminal. Replace the following with your own values.
|
||||||
|
`YOUR_VPN_SERVER_IP_OR_DNS_NAME` is your VPN server IP or DNS name.
|
||||||
|
`IMPORTED_CERTIFICATE` is the name of the certificate from step 2 above, e.g. `vpnclient.p12_0`
|
||||||
|
(the one flagged with KT - Priv. Key Trusted - if not flagged as KT, import certificate again).
|
||||||
|
`THESE_ADDRESSES_GO_THROUGH_VPN` are the local network addresses that you want to browse through the VPN.
|
||||||
|
Assuming that your local network behind RouterOS is `192.168.0.0/24`, you can use `192.168.0.0/24`
|
||||||
|
for the entire network, or use `192.168.0.10` for just one device, and so on.
|
||||||
|
|
||||||
3. Run these in terminal, replace YOUR_VPN_SERVER_IP_OR_DNS_NAME with your server ip/dns,
|
|
||||||
IMPORTED_CERTIFICATE is the certificate that you get on step 2 something like certificate.p12_0
|
|
||||||
(the one flagged with KT - Priv. Key Trusted - if not flagged as KT, import certificate again)
|
|
||||||
and THESE_ADDRESS_GO_TRHOUGHT_VPN with the addresses that will browse through the VPN,
|
|
||||||
assuming your network is in that range that you can use 192.168.0.0/24 for the entire network,
|
|
||||||
or 192.168.0.10 for just one client, and so on
|
|
||||||
```bash
|
```bash
|
||||||
/ip firewall address-list
|
/ip firewall address-list
|
||||||
add address=THESE_ADDRESS_GO_TRHOUGHT_VPN list=local
|
add address=THESE_ADDRESSES_GO_THROUGH_VPN list=local
|
||||||
/ip ipsec mode-config
|
/ip ipsec mode-config
|
||||||
add name=ike2-rw responder=no src-address-list=local
|
add name=ike2-rw responder=no src-address-list=local
|
||||||
/ip ipsec policy group
|
/ip ipsec policy group
|
||||||
@ -443,12 +444,12 @@ or 192.168.0.10 for just one client, and so on
|
|||||||
/ip ipsec proposal
|
/ip ipsec proposal
|
||||||
add name=ike2-rw pfs-group=none
|
add name=ike2-rw pfs-group=none
|
||||||
/ip ipsec identity
|
/ip ipsec identity
|
||||||
add auth-method=digital-signature certificate=IMPORTED_CERTIFICATE.p12_1 generate-policy=port-strict mode-config=ike2-rw \
|
add auth-method=digital-signature certificate=IMPORTED_CERTIFICATE generate-policy=port-strict mode-config=ike2-rw \
|
||||||
peer=ike2-rw-client policy-template-group=ike2-rw
|
peer=ike2-rw-client policy-template-group=ike2-rw
|
||||||
/ip ipsec policy
|
/ip ipsec policy
|
||||||
add group=ike2-rw proposal=ike2-rw template=yes
|
add group=ike2-rw proposal=ike2-rw template=yes
|
||||||
```
|
```
|
||||||
1. Verify in your certificates panel. You will see 2 files, the one that is marked KT is the key. See [#1112](https://github.com/hwdsl2/setup-ipsec-vpn/issues/1112#issuecomment-1059628623) for more details.
|
4. For more information, see [#1112](https://github.com/hwdsl2/setup-ipsec-vpn/issues/1112#issuecomment-1059628623).
|
||||||
|
|
||||||
> tested on
|
> tested on
|
||||||
> mar/02/2022 12:52:57 by RouterOS 6.48
|
> mar/02/2022 12:52:57 by RouterOS 6.48
|
||||||
|
|||||||
BIN
docs/images/routeros-get-cert.gif
Normal file
BIN
docs/images/routeros-get-cert.gif
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 671 KiB |
BIN
docs/images/routeros-import-cert.gif
Normal file
BIN
docs/images/routeros-import-cert.gif
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 1.0 MiB |
Loading…
Reference in New Issue
Block a user